Automated Teller Machines (ATMs) has made banking far more easier for both the banks and the customers. However, Bank servers are now being compromised to trick these highly secured ATMs into spewing out cash without the bank knowing.
The United State Computer Emergency Readiness Team (US-CERT) has released a joint technical alert from the Department of Homeland Security (DHS), the Federal Bureau of Investigation and the Treasury, warning about a new ATM scheme being used by the North Korean APT hacking group known a the Hidden Cobra.
In one incident in 2017, the hacking group enabled cash to be withdrawn from ATMs located in 30 different countries. Likewise in 2018, 23 different countries have been affected throughout Africa and Asia.
The hacking group believed to be backed by the North Korean Government is also known as the Lazarus Group and Guardians of Peace. The group has previously been linked with a number of attacks on a number of media agencies, aerospace, financial and critical infrastructure sectors worldwide.
The group has recently been reported to have links with the WannaCry ransomeware problem last year that shut down hospitals and big businesses worldwide. They have also been linked with SWIFT Banking attack in 2016 and the Sony pictures hack in 2014.
Now, the Department of Homeland Security (DHS), the Federal Bureau of Investigation and the Treasury Department, in the United States have released details about a new cyber attack, and it is called “FASTCash“. It is reported that Hidden Cobra has been using “FASTCash” malware to cash out ATMs since at Least 2016 by compromising the bank servers in Africa and Asia.
Description of “FASTCash” Malware
According to the Technical Analysis carried out by US-CERT, FASTCash malware attacks compromises the bank’s server switch application within the targeted bank to facilitate fraudulent transactions.
The switch application server is a core component of ATMs and Point-of-Sales (POS) infrastructure, it is responsible for validation of a user’s bank account details for a requested transaction. The applications is prompted when you use an ATM or POS and validate your transaction, rejecting or accepting it, based on your bank account balance.
Hidden Cobra has however managed to compromise the switch application servers at different banks using accounts having minimal account activity or zero balances. The attackers are believed to be intercepting transaction requests with fake but legitimate approval response without actually validating available balance with the switch. This happens without the bank being notified.
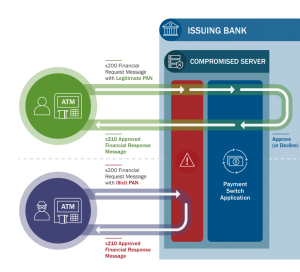
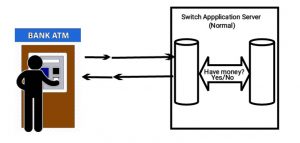
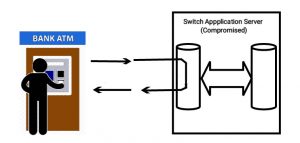
How The Bank Servers Are Being Compromised
Analyst have said although the initial infection vector used to compromise the Bank Network is still unknown, the attackers used phishing or malicious emails containing a windows based malware against bank employees. This allows the attackers to move laterally through a bank’s network and illicitly access the switch application server. While most compromised servers were found to be running Unsupported IBM Advanced Interactive eXecutive (AIX) operating system versions, analyst reported no form of vulnerability exploitation in AIX operating system.
Recommendations for Protections
- The US-CERT recommends that banks’ IT administrators make two-factor authentication mandatory before any access to switch application server.
- US-CERT has also made copies of IOCs (Indicators of Compromise) available for download, to help enable network defenses
- Maintain up-to-date antivirus and engines.
- Keep operating system patches up-to-date.
- Disable file and printer sharing services. If these services are required, use strong passwords or Active Directory authentication.
- Restrict users’ ability (i.e., permissions) to install and run unwanted software applications. Do not add users to the local administrators group unless required.
- Enforce a strong password policy and require regular password changes.
- Exercise caution when opening email attachments, even if the attachment is expected and the sender appears to be known.
- Enable a personal firewall on organization workstations, and configure it to deny unsolicited connection requests.
- Disable unnecessary services on organization workstations and servers.
- Scan for and remove suspicious email attachments; ensure the scanned attachment is its “true file type” (i.e., the extension matches the file header).
- Monitor users’ web browsing habits; restrict access to sites with content that could pose cybersecurity risks.
- Exercise caution when using removable media (e.g., USB thumb drives, external drives, CDs).
- Scan all software downloaded from the internet before executing.
- Maintain situational awareness of the latest cybersecurity threats.
Have something to say? Please comment below and share




